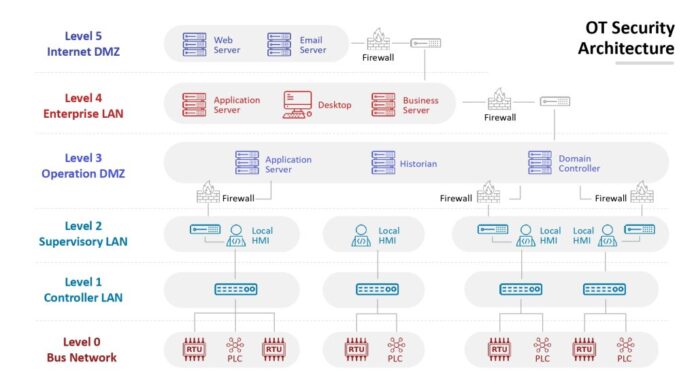
The key pillar of digitalization is secure communication and data exchange between Information Technology (IT) and Operational Technology (OT). However, these environments have distinct architectures, protocols, and security requirements. To ensure a reliable and secure data exchange, it is essential to consider the specific and distinct requirements of industrial networks, IoT devices, and office networks.
Throughout the past decade, OT systems have become more IP-connected, making them more vulnerable to cybersecurity threats and OT cyberattacks. In this case, enterprises must incorporate OT cyber risk management into their overall cybersecurity strategy.
Nearly 70% of industrial firms had an OT cyber-attack last year. According to ABI Research, Industrial organizations need an integrated and cyber-resilient IT-OT framework to address this increasingly sophisticated threat landscape.
Industrial operations are becoming more vulnerable cyber risks in OT and IoT environments. This has led to adverse business impacts, resulting in operational shutdowns and significant revenue losses. In addition, industrial operators also need to address the challenges and risks associated with the adoption of the latest technologies such as AI in cybersecurity, robotic automation, cloud security, 5G networks, and more. This necessitates the shift towards zero-trust security implementation, selecting the right provider with deep expertise in both OT and IT environments.
Continue reading the blog to learn about OT, its significance, how it differs from IT, and the role of IoT in OT, the key difference between OT and IoT security.
What Is Operational Technology (OT)?
OT comprises the hardware and/or software that controls or monitors physical assets and processes. This consists of traditional Industrial Control Systems (ICS) to Internet of Things (IoT) devices that are included in a physical process. This comprises technologies such as Supervisory Control and Data Acquisition (SCADA) systems, Programmable Logic Controllers (PLCs), and Distributed Control Systems (DCS). OT is essential in industry segments such as manufacturing cybersecurity, energy security, utilities, transportation, and more.
The term OT often relates to factories or electrical grids. However, OT is now ubiquitous across nearly every industry, ranging from HVAC systems, escalators, and elevators to drones, cranes, and autonomous robots — all these falls under the umbrella of OT.
Enterprises can gain more benefits with the integration of OT with IT infrastructure. The key drivers of IT and OT convergence include Data Utilization, Efficiency and Automation, and Cost Reduction.
Traditionally, IT and OT have operated independently (in separate silos), each with its own set of protocols, standards, and cybersecurity measures. The rise of Industrial Internet of Things (IIoT) enhanced the convergence of OT and IT. However, this convergence also exposes OT systems to the same cyber threats that IT systems face.
Calsoft and SmartHub.ai have joined forces to deliver an integrated edge solution that strengthens visibility, automation, and resilience across OT infrastructures—from factory floors to large campuses—confronting rising cyber threats, compliance demands, and downtime costs.
Let us now explore OT security and its significance.
What is OT Security, and why is it important?
OT systems are safety-critical systems as latency or delay cannot be tolerated, which leads to significant operational issues or safety hazards. Therefore, any cybersecurity measures for OT systems that bring delay are not suitable.
The implementation of strong security protocols is necessary to protect against diverse cyber threats and vulnerabilities in OT environments. OT security solutions mean protecting OT systems, including SCADA systems and ICS, guaranteeing they are resistant to unauthorized access and cyber threats while sustaining operational continuity.
The key vulnerabilities of OT systems are:
- OT systems have become more open
- Cybersecurity is not considered in most OT component designs
- The rise of IoT, IIoT, and digital transformation has increased network connectivity, leading to IoT security loopholes
- Lack of cybersecurity awareness among OT users and administrators
Although OT and IT security intersect in some areas, OT’s unique operational requirements and system architectures demand a fundamentally different industrial security approach
Gain more insights on OT security and IT-OT convergence in our latest industry report OT Security: A Complete Guide and Playbook
Download OT Security Industry Report
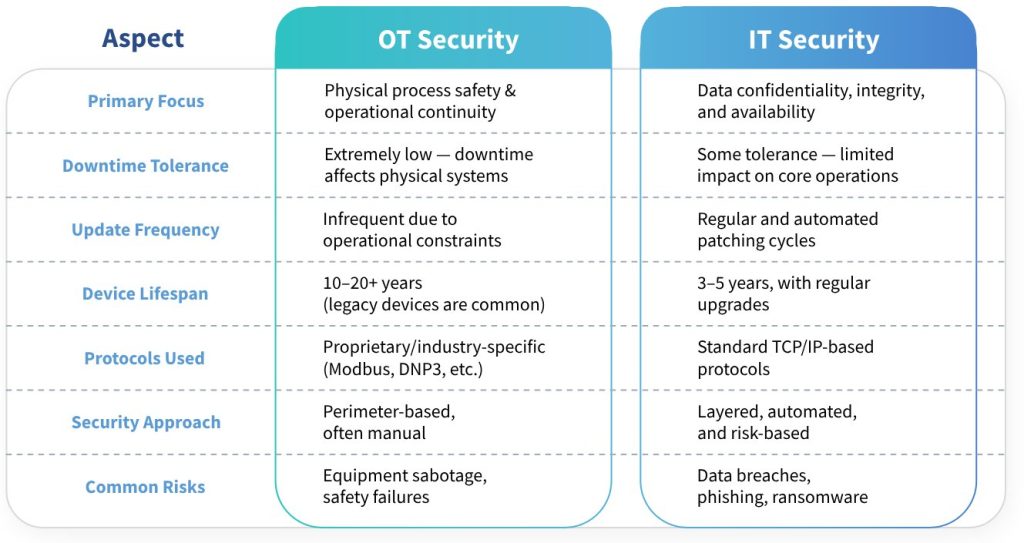
OT Security vs IT Security
Emerging Technologies That Impact OT Security
Several technologies are transforming OT environments, offering benefits but also introducing new risks:
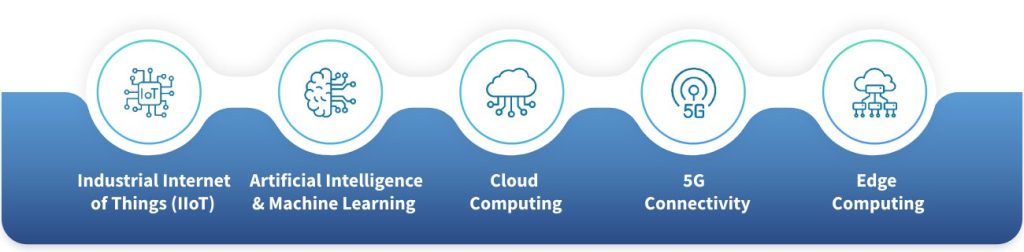
- Industrial Internet of Things (IIoT): Increases connectivity but expands the attack surface significantly.
- Artificial Intelligence & Machine Learning in OT Security: Enhances anomaly detection and predictive maintenance but relies heavily on secure data inputs.
- Cloud Computing security: Enables centralized data management but introduces concerns around secure data transfer and storage.
- 5G Connectivity: Accelerates real-time remote control and monitoring, making latency-critical systems more exposed.
- Edge Computing security: Improves local processing but requires robust endpoint security strategies.
Key Strategies for Robust OT Security
To ensure resilience and compliance in OT systems, organizations should implement the following best practices:
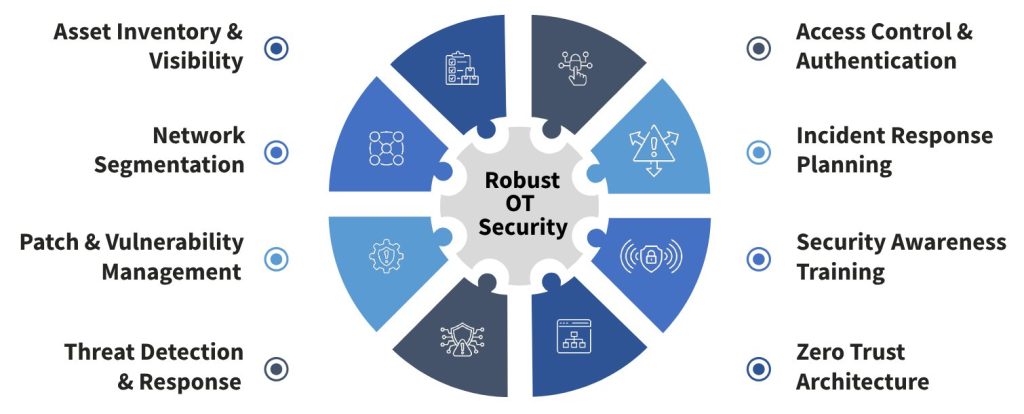
Asset Inventory & Visibility: Map all OT devices and maintain updated records of their firmware and configurations.
Network Segmentation for OT and IoT Security: Isolate critical OT assets from IT networks using VLANs, DMZs, and firewalls.
Patch & Vulnerability Management: Apply vendor-approved patches carefully or use virtual patching for legacy devices.
Threat Detection & Response in OT environments: Use behaviour-based monitoring and OT-specific threat intelligence to detect anomalies.
Access Control & Authentication: Enforce least privilege policies, multi-factor authentication, and role-based access.
Incident Response Planning: Develop OT-specific response playbooks and test them regularly with stakeholders.
Security Awareness Training for OT Operators: Train OT staff on cybersecurity hygiene, phishing detection, and secure device use.
Zero Trust Architecture in OT/IoT: Adopt a security model where every device and user must continuously prove trustworthiness.
Conclusion: It’s Time to Prioritize OT Security
As digital transformation drives IT-OT convergence, the traditional boundaries that once separated operational and information technologies have blurred. While this unlocks new opportunities for efficiency and innovation, it also introduces unprecedented cybersecurity challenges for OT and IoT environments.
By implementing robust OT cybersecurity frameworks—grounded in best practices and supported by emerging technologies—organizations can safeguard operations, reduce risk, and ensure long-term resilience.
FAQ’s
Q1: What makes OT security different from IT security?
A. OT security focuses on maintaining physical process uptime and safety, while IT security is concerned with protecting data confidentiality and integrity. OT systems often can’t tolerate downtime, making traditional IT security measures unsuitable.
Q2: Why is OT becoming more vulnerable to cyberattacks?
A. Due to increased connectivity (IoT/IIoT), legacy equipment, and lack of built-in security in older systems, OT networks now face more sophisticated threats similar to IT environments.
Q3: Can I apply IT security tools directly to OT systems?
A. Not always. Many IT security tools can disrupt OT operations or introduce latency. Instead, organizations should use OT-aware security solutions designed for industrial environments.
Q4: What is Zero Trust in OT?
A. Zero Trust for OT involves validating every user, device, and action in the network, regardless of origin, and granting access only when necessary.
Q5: How do I start improving OT security in my organization?
A. Begin by conducting a comprehensive asset inventory, assessing risks, implementing segmentation, and building an OT-specific incident response plan.
The post Securing the Future: Cybersecurity for OT and IoT Environments appeared first on Calsoft Blog.